A mining machine is a piece of equipment used in the mining industry to extract minerals, ores, and other geological materials from the earth. These machines are designed to dig, drill, and transport materials from one location to another in the mining process. They can be used for surface mining or underground mining, depending on the type of deposit being mined. Some common types of mining machines include Crushing Equipment, Grinding Equipment, haul trucks, drills, and Other Mining Machines. These machines are essential for efficient and productive mining operations. Mining Machine,Jaw Crusher Machine,Hammer Crusher Machine,Mining Machine Rod Mill Shenyang North Heavy Metallurgical Engineering Technology Co., Ltd. , https://www.nhmetallurgy.com
Indeed, the research and development of the Internet of Things should take the form of teamwork and division of labor. Therefore, there are exclusive posts for embedded devices, gateways, web front-ends, APPs, and back-end developments. As a system architect, you naturally need to master the key technologies of various positions. As an embedded engineer, mastering network programming and web programming can greatly expand his horizons and architectural thinking, and can actively propose optimization opinions on various protocols and application scenarios of the system, rather than just accept assignments. At a minimum, it is possible to quickly build an IoT demo system without relying on back-end engineers. Therefore, mastering some basic network programming and web programming skills is very important for improving the development capabilities of IoT R&D engineers.
This article can be considered as the first original technology sharing of the embedded penguin circle's WeChat Wifi access solution. The technology sharing of the WeChat Wifi access solution series will be publicized after the Spring Festival in 2016, so stay tuned. This article gives an overview of the knowledge involved in the Internet of Things, followed by detailed guidance on the development of the article.
First, OSI seven-layer model and TCP/IP four-layer model
The OSI seven-layer model is a theoretical research model of a network protocol, or it can be called an ideal model. The TCP/IP four-layer model is a de facto standard and is a widely used model. The association between the two is illustrated as follows: 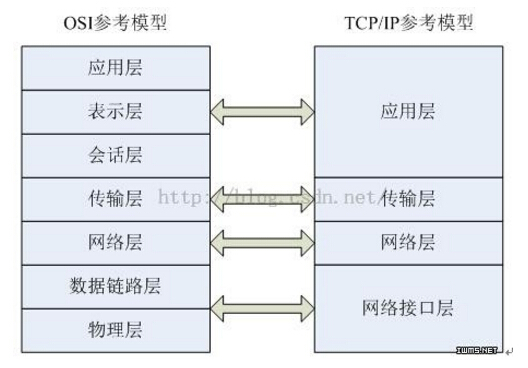
For the interpretation of the two models, I would like to say that as developers do not have to force to understand the meaning of the various layers, such as what the session layer is responsible for, and what the presentation layer is responsible for. When you do not deal with the problems solved by these levels in the development process, it is more difficult for you to understand and remember. However, when you encounter problems and need to resolve, you must be very clear about the responsibilities at these levels.
A very critical factor in measuring the practicality of an IoT platform or protocol is its message reach capability, which directly impacts IoT application development. Therefore, we analyze the TCP/IP de facto standard model from the message reach capability. We imagine the following scenarios and analyze them. 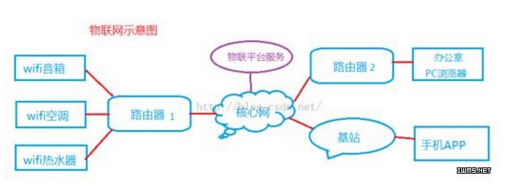
1. Network interface layer. The router 1 and the wifi speaker, the air conditioner, and the water heater form a home area network, and communicate using the wifi (802.11) protocol. The protocol defines physical signals, data frame formats, packet loss retransmission mechanisms, flow control, and so on. These are the tasks of the network interface layer. Also, multiple devices share channels, and sending data at the same time creates a conflict and how it is resolved. This is also the content of the network interface layer. In fact, IoT engineers do not have to care about this content. Because the content of the wifi physical signal is the responsibility of the wifi chip manufacturer, the wifi single chip (wifi+SOC) will provide the SDK package and provide the SOCKET programming interface. Therefore, the focus of our responsibilities is to focus on programming development knowledge above the network level.
2. The network layer, that is, the IP protocol, the most basic understanding is that each IP corresponds to an IoT device, a cell phone, or a back-end server. In principle, a network card corresponds to an IP, as shown in the wifi speaker, wifi water heater have an independent IP. The communication between the networks is based on IP. The network packets are finally sent to the device corresponding to the target IP through the router.
Wifi speakers and other home devices joined the home LAN, in fact, each obtained a LAN IP, 192.168.*.*, including the router 1 also has a LAN address, but the router 1 also has an Internet IP. Only the router's Internet IP can be known to the outside world. The outside world cannot know which device corresponds to the LAN IP. Only router 1 knows it. Therefore, the source IP of all outgoing packets is the Internet IP of router 1. The destination IP of the packet to the device is also the router's Internet IP.
We all know that when the device goes online, it needs to inform the IoT platform server of its own status in order to facilitate user control. Therefore, the IP of the Internet of Things platform server must be an Internet IP or a domain name (the DNS protocol can resolve the domain name to IP). If it is a LAN IP, it is impossible to access the device.
Here, we must also remember that the first communication between the device and the IoT platform should always be initiated by the device, because even if the IoT platform knows the public IP of Router 1, it cannot send messages to the internal device. of. In addition, the server must continue routing the device to reach the last hop of the IoT routing information, because the process of routing information in the original route has the information sent by the router 1 to record which device it is sending. If you do not record this information, the Internet Protocol IP of router 1 alone cannot reach the specific device.
If you can't understand the above passage, remember that the IoT platform's initiative to send a message to the device via the Internet IP of Router 1 is unsuccessful. However, when the device sends a message to the IoT Platform, the IoT Platform will directly Response to the packet (IP source address and destination address swap location) is reachable to the device. If it is a way to satisfy the question and answer, then the server does not need to record this routing information. If it needs to satisfy the scenario that the server actively sends messages to the device, the server needs to record this information.
In addition, we know that network devices physically represent a real network card. The MAC address of the network card is 6 bytes and 48 bits. In a LAN communication, network programming is based on the IP address, the router or switch how to find the corresponding MAC address through the IP address, that is, ARP address resolution protocol, this is the network layer's responsibilities, but as a developer, We understand it.
3. Transport layer, ie TCP/UDP protocol. For the transport layer, we need to understand that the use of the network running on a PC or mobile phone may be many, but they all correspond to the same IP. How does the operating system distribute a data packet to the corresponding network application? This depends on the port defined by the transport layer. Common network application layer protocols will default to the transport layer port number, such as 21 for FTP, 80 for HTTP, 25 for SMTP, and so on. In addition to defining the port number, the transport layer has two very important protocols, TCP connection-oriented protocol and UDP packet protocol. The former can be understood as a virtual telephone connection protocol. Once both parties make a call to establish a connection between the two parties, all data packets follow the same routing path. Because the connection-oriented protocol guarantees resources in the bandwidth, the connection-oriented protocol guarantees quality. Therefore, it is applicable to some network applications that require stringent data quality, such as e-mail applications. If the quality is not guaranteed, the content of the e-mail is Who can use this email system if it is not guaranteed to be correct? However, for some audio and video applications, dropping one or two frames does not affect the user experience at all, then UDP protocol will be used. It is not connection-oriented, and routing information before sending can be used. Not saved, it is delivered using best effort (ie try my best).
4. Application layer. Common web application protocols include HTTP, FTP, SMTP, POP, and so on. Embedded IoT applications are based on these network application protocols. These protocols regulate the basic format of request connection, response and data transmission. As an embedded Internet of Things application, it should define the format of the application protocol itself. These data formats can be easily customized or can use mature standard formats such as HTML, XML, JSON, and so on. Because firewalls typically only release HTTP packets at port 80, Internet of Things applications are generally built on top of HTTP.
Therefore, we must distinguish between web application layer protocol HTTP and application custom protocol. The latter uses the former for transmission communication. Regardless of which format is used by the application custom protocol, both parties need to use the communication simultaneously. When the IoT device and the IoT platform communicate in the background, a simple XML format or JSON format can be used, and the IoT platform is also accessed by the PC browser. Therefore, since the browser only supports the HTML format, the IOT platform is required to provide Content services in HTML format, the same way, communication between the Internet of Things platform and mobile phone APP can use XML or JSON. Even, we can customize the simple commands to implement the functions, but using XML or JSON formats helps the data to have good readability, and there is also a mature library to explain.
These are based on the HTTP web application protocol.
Second, socket programming
Socket programming is divided into two ways: TCP and UDP. Are as follows: 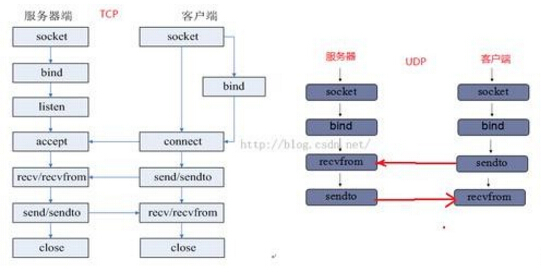
It can be seen that TCP/UDP socket sockets need to bind IP and port addresses before communication. For TCP, the server needs to listen to listen first. After the client initiates the connect request, the server can accept. Then the connection-oriented communication environment is established and communication is performed through the send/recv function.
And UDP programming is very simple, can start data transmission immediately after binding.
In addition to basic socket programming, you also need to know the following:
1) Blocking and non-blocking. Network sockets are blocked and non-blocking. If it is assumed that the created socket is blocked, its recv function must wait until the other party transmits data before it returns. Otherwise it will remain in a blocked state. The non-blocking state is to immediately see if there is data in the buffer. If there is data returned, no error will be returned instead of being dead. Blocking mode can be simply understood as synchronous mode of operation, while non-blocking mode can be understood as asynchronous mode of operation.
2) Multiplexing. As a server, there may be multiple client connections. If you poll each client socket for data, it would be more efficient. Socket programming's select and poll interfaces are used to solve this type of multi-channel IO multiplexing problem. It can simultaneously detect multiple connected data communications.
Third, B/S and C/S
1.B/S is browser and client mode, using HTML grammar format. It uses a question and answer, that is, the server is stateless, it does not know whether the client has previously visited. Statelessness helps the server to serve efficiently and steadily. But the impact of this model on IoT applications is fatal. Because the server can't actively send messages to IoT devices. So how can we improve it?
1) Ajax technology. The latest Ajax technology is to solve the frequent problem of partial page refresh. That is, the local data of an HTML page is changed. Before ajax, a request is sent again to refresh the entire page. The ajax is simply sending changes to the server request. The former will see the page flicker when requested, while the latter will not. We can just use ajax to periodically initiate a request to the server and ask the server if there is any updated data. If the query frequency is high, then the real-time effect is good, but it will increase the server burden. In essence, it is still a form of question and answer instead of two-way communication. Ajax requires browser technical support.
2) web socket technology. Web socket is proposed to solve the two-way communication problem of HTML. After the first HTTP request, the server will let the server update the subsequent protocol to the Web socket for communication. Web socket requires tom cat 7.0 or more to run container technical support.
The Internet of Things application development can emulate the HTTP protocol through socket programming on the device side. It can also emulate HTML, XML, or Web socket over HTTP.
C/S client and server programming was thought to have been gradually replaced by B/S before the advent of smart machines in the PC desktop area, but it was reborn on the smart device side. Despite the rapid development of HTML5, personally, the experience of browsers on smart devices such as mobile phones is still inferior to native APP. The bigger advantage of HTML5 is its portability.
C/S programming can use socket communication to communicate directly, so naturally there is no problem of communication between the two parties. If C/S programming uses http libraries for programmatic communication, it also has the problem of two-way communication.
At present, many people hope to use the J2EE business architecture to support the Internet of Things. However, after all, IoT devices have limited resources. Some terminals may be simple SCMs. It is difficult to run the full TCP/UDP protocol. A simplified version of the TCP/IP protocol is proposed, such as Co AP (a synonym for Constrained Application Protocol), ucIP, LWIP, and so on. From the perspective of business application agreements, IBM's R&D MQTT may become the standard for IoT application protocols.
Fourth, Web programming
The first thing Web programming refers to is the syntax programming of the browser display content. Web static language is HTML.
1.HTML does not support dynamic changes in data. Therefore, a dynamic language based on the interpretation engine such as ASP, PHP, JSP, etc. is produced. Such languages ​​use HTML/CSS to describe presentation styles, and use dynamic languages ​​to control the presentation of data, such as accessing databases for new data, and so on.
Need to know, ASP, PHP, JSP these languages ​​are server programming languages, when the user accesses the server corresponding webpage through the browser, the content of the webpage ASP/PHP/JSP will be converted into specific data through the server's interpreter engine, and finally The other HTML and CSS data are returned to the browser for presentation. Therefore, the browser will always be sure of HTML, CSS, and data. There are no ASP/PHP/JSP statements.
2.javascript script. The script is the syntax of the browser's technical support, not the server's technical support. For example, a login interface, to ensure the correctness of user input, such as irregular characters, length is too long, etc., generally use javascript script to detect, without sending a request to the server. The ajax technology mentioned above is also a scripting technology supported by the browser.
3. jQuery, which encapsulates javascript technology, enables better front-end programming control.
4. HTML/CSS/JS scripts, called web front-end programming development, and ASP/JSP/PHP, etc. for back-end development.
5. Back-end development will naturally involve database access, business logic, and it needs to interact with the front-end. Therefore, the web application programming architecture generally uses the MVC programming model, ie M is the data model and is responsible for database access; V is the view and is responsible for presentation; C is the control. The MVC model enables a good separation of presentation from the database and facilitates application development.
6. As a whole running architecture to understand, the server needs to include a database (such as mysql), web application and interpretation engine, and web services (such as apache and tom cat). Apache provides http services.
7. The basis of JSP is JAVA syntax. The J2EE architecture provides servlet technology for supporting network applications. JSP is actually a high-level encapsulation of servlets and appears as an independent technology. JSP focuses on supporting B/S aspects of network applications, while servlets support C/S mode network applications through mapping classes, such as WeChat Bluetooth access. The back-end technology of wifi access is supported using servlets, and the top layer uses XML/JSON format.
A Survey of Web Programming in Internet of Things Network Programming
This article is based on the embedded IoT R&D engineer's vision for network programming and web programming. For children shoes focused on J2EE back-end service development, this article may be a bit simpler. But network programming and web programming are a vacuum for most embedded IoT engineers.